Data Security Services Can Be Fun For Everyone
Table of ContentsRumored Buzz on Data Security ServicesData Security Services for Beginners6 Easy Facts About Data Security Services DescribedThe Ultimate Guide To Data Security ServicesThe Of Data Security Services4 Easy Facts About Data Security Services Described
It gives homeowners the right to recognize which data are gathered regarding all of them and also to stop the sale of their information (data security services). CCPA is actually a clear solution, relating to for-profit associations that carry out organization in The golden state and satisfy among the observing criteria: making even more than fifty percent of their yearly revenues coming from marketing customers' individual relevant information; making gross revenues of much more than $50 million; or even keeping individual info on greater than 100,000 buyers, families, or even units.Many are actually making an effort to apply future-proof answers. Rather than meeting CCPA requirements only in California, Microsoft is applying all of them to all United States consumers, though other states do not yet have plans as selective as the CCPA. This method will most likely end up being a lot more popular, as a lot of companies are utilizing the absolute most selective lawful requirements as their own criterion.
Yet another challenging part of privacy guideline pertains to the deletion and porting of data: regulations permit customers to ask for that their records be deleted or that business provide customer data to specific consumers or even other services. For many companies, these duties are technically difficult. Corporate records sets are often ragged throughout different IT structure, creating it hard to recoup all relevant information on specific consumers.
Data Security Services Fundamentals Explained
The best techniques account for the different categories of records, which can easily call for different storing plans. Offered the spreading of state-of-the-art machine-learning devices, a lot of companies will definitely find to analyze the higher amounts of records they pick up, specifically by experimenting along with without supervision formulas.
Leading organizations have actually cultivated identity- and access-management strategies for individuals according to their roles, along with security-access levels established for different records classifications. About one-third of the violations in recent times have actually been actually credited to expert risks. This risk may be minimized through ensuring that information sets come only to those who require all of them which nobody has accessibility to all available information.

Examine This Report on Data Security Services
Firms must build clear, standard treatments to govern ask for the elimination or transactions of information. These must make certain fast observance along with regulations and deal with customer requests for the identification, extraction, and also transactions of data. The methods need to assist information discovery in every pertinent facilities environments within a provider as well as across its own affiliates.
Security as well as privacy end up being nonpayment alternatives for individuals, while functions hit a balance along with the user expertise. It is vital for organizations to interact transparently: consumers ought to recognize when and why their information are actually being accumulated. A lot of business are actually adding buyer personal privacy to their market value proposals and also very carefully crafting the information in their personal privacy plans as well as biscuit notifications to line up along with the general company.
Business may as a result differentiate themselves by taking calculated, good steps in this particular domain. In our knowledge, individuals respond to firms that manage their individual data as thoroughly as they do on their own.
The Buzz on Data Security Services
All it takes is actually someone to weaken a website or even system. Without thorough safety Get More Info at both the consumer and venture degrees, you are practically guaranteed to become in jeopardy. Defending your own self and also others starts with knowing how a data violation takes place. The expectation is actually that a record breach is triggered by an outdoors cyberpunk, but that is actually certainly not always real.
This individual intentionally accesses and/or discusses records along with the intent of inducing danger to a private or firm. The destructive expert may have legit certification to use the data, but the intent is to utilize the relevant information in dubious means. An unencrypted and also uncovered laptop pc or external difficult disk everything which contains vulnerable relevant information goes missing.
Your unit's system software, software application, equipment, or the network and also web servers you're connected to can possess security flaws. These voids in protection are found through offenders try here as the perfect place to push malware in to. Spyware particularly is actually optimal for swiping private data while being totally unseen. You could not find this disease up until it is actually late.
Fascination About Data Security Services
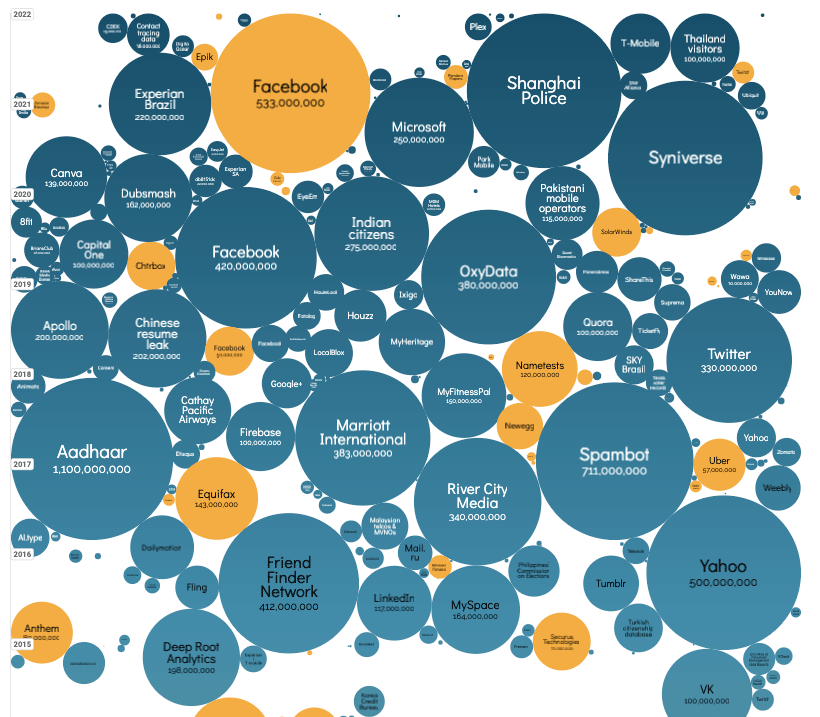
When you are actually making an effort to consider how to prevent records violation strikes or even leakages, protection is actually just click over here now as sturdy as the weakest hyperlink. Listed here are actually a couple of absolute best practices to avoid an information violated as quickly as options are on call.
This website makes use of biscuits to strengthen your knowledge. If you have any questions about our plan, our company invite you to find out more. Accept
The Basic Principles Of Data Security Services
There are countless kinds of cyber protection and safety analytics, all paid attention to finding as well as strengthening methods to stop unwarranted access to or damaging data. These two terms are actually frequently utilized reciprocally, yet they're not fairly the exact same. Relevant information safety, or even infosec, is actually worried about keeping relevant information confidential and available, despite whether that info is stored electronically or even in bodily type.